Concealing Mac files is a common practice for many users who want to keep their information private and secure. There are various methods and tools available that can help in hiding files on a Mac computer. One popular method is to use the built-in feature of the operating system, which allows users to hide files and folders by simply selecting the “hidden” option in the file properties.
This method is easy to use and effective in keeping files out of sight from prying eyes. Another method is to use third-party software that offers more advanced features for concealing files, such as encryption and password protection. These tools provide an extra layer of security for sensitive information and ensure that only authorized users can access the hidden files. Overall, concealing Mac files is a personal choice that can help users protect their privacy and keep their data safe from unauthorized access.
Reasons for Hiding Files
There are several reasons why someone may choose to hide files on their computer or other devices. One common reason is privacy concerns. People may have sensitive information stored in their files that they do not want others to see. This could include personal information such as financial records, medical records, or personal correspondence. By hiding these files, individuals can feel more secure knowing that their private information is not easily accessible to others.
Another reason for hiding files may be to protect sensitive business information. Companies may have proprietary information or trade secrets that they want to keep confidential in order to maintain a competitive advantage. By hiding these files, businesses can prevent unauthorized access and protect their valuable intellectual property. Additionally, some individuals may hide files simply to keep their digital workspace organized.
With the amount of data that people accumulate on their devices, it can be easy for files to become disorganized and difficult to find. By hiding files that are not frequently used or that are not relevant to current projects, individuals can streamline their digital workspace and make it easier to access the files that are most important to them. Overall, hiding files can be a practical way to protect privacy, safeguard sensitive information, and maintain a more organized digital environment.
Hiding Files on Mac
Hiding files on a Mac computer can be a useful tool for maintaining privacy and organization. By hiding certain files, users can keep sensitive information out of view from prying eyes or simply declutter their desktop or folders. This can be particularly helpful for individuals who share their computer with others or work in a shared workspace. Hiding files can also help prevent accidental deletion or modification of important documents.
Additionally, hiding files can be a way to keep personal or work-related information separate and easily accessible when needed. While some may argue that hiding files can be a form of secrecy or misdirection, it ultimately comes down to personal preference and the specific needs of the user. As long as the files are stored securely and can be easily retrieved by the owner, hiding files on a Mac can be a practical solution for maintaining privacy and organization.
With the various options available for hiding files on a Mac, such as using the built-in file attributes or third-party applications, users have the flexibility to choose the method that best suits their needs. Ultimately, the decision to hide files on a Mac is a personal one that can help streamline workflows and protect sensitive information.

Keyboard Shortcuts Method
The Keyboard Shortcuts Method is a technique used by individuals to increase their efficiency and productivity when using a computer. By memorizing specific key combinations that perform certain functions, users are able to navigate through programs and complete tasks more quickly than using a mouse or touchpad.
This method is widely utilized in various industries such as graphic design, programming, and data entry, where time is of the essence. By incorporating keyboard shortcuts into their workflow, individuals are able to streamline their processes and focus on the task at hand without the distractions of searching for specific functions or commands. While some may argue that relying solely on keyboard shortcuts can be limiting in certain situations, many users find that this method greatly enhances their overall computer experience.
With practice and dedication, individuals can become proficient in using keyboard shortcuts and significantly improve their efficiency in completing tasks on their computers. Ultimately, the Keyboard Shortcuts Method is a valuable tool for those looking to optimize their workflow and make the most of their time spent on a computer.
Activating FileVault
Activating FileVault on your device is a security measure that helps protect the data on your computer or laptop. By encrypting the files on your device, FileVault makes it more difficult for unauthorized users to access your personal information. This can be especially important if you store sensitive data on your device, such as financial information or personal documents. Activating FileVault is a proactive step you can take to enhance the security of your device and safeguard your information from potential threats.
While it may require some initial setup and possibly some additional time to encrypt your files, the peace of mind that comes from knowing your data is protected is well worth the effort. Additionally, activating FileVault can also help ensure your compliance with any data protection regulations that may apply to your industry or region. Overall, enabling FileVault is a smart choice for anyone looking to enhance the security of their device and protect their personal information from unauthorized access.

Third-Party Tools
Third-party tools are software applications developed by individuals or companies that are not affiliated with the original creators of a platform or system. These tools are often created to enhance or extend the functionality of existing software or services. They can provide additional features, customization options, or automation capabilities that are not available in the original product.
While some third-party tools are officially supported by the platform they are designed for, others may operate independently and may not be endorsed by the original developers. Users may choose to use third-party tools to improve their productivity, streamline workflows, or access additional resources that are not available through the original software. However, it is important for users to exercise caution when using third-party tools, as they may not always be secure or reliable.
It is recommended to research the reputation and credibility of the developer before downloading and installing any third-party tools, as they may pose potential risks such as malware, data breaches, or compatibility issues. Ultimately, third-party tools can be valuable resources for users looking to enhance their digital experience, but it is crucial to approach them with vigilance and awareness of the potential risks involved.
Utilizing Parallels Toolbox
Parallels Toolbox is a powerful software suite that offers a wide range of productivity tools to help users streamline their daily tasks and optimize their workflow. By utilizing Parallels Toolbox, users can easily access and utilize a variety of tools such as screen recording, video conversion, and file management. These tools can help users save time and effort by automating repetitive tasks and simplifying complex processes.
Additionally, Parallels Toolbox offers a user-friendly interface that makes it easy for users to navigate and access the tools they need quickly and efficiently. With its extensive range of tools and features, Parallels Toolbox is a valuable asset for individuals and businesses looking to increase their productivity and efficiency. Whether you are a student, freelancer, or professional, Parallels Toolbox can provide you with the tools you need to stay organized, focused, and productive in your daily tasks.
Whether you are looking to convert a video file, capture a screenshot, or clean up your computer’s storage, Parallels Toolbox has you covered with its comprehensive suite of tools. Overall, Parallels Toolbox is a versatile and user-friendly software solution that can help users optimize their workflow and enhance their productivity in a variety of ways.
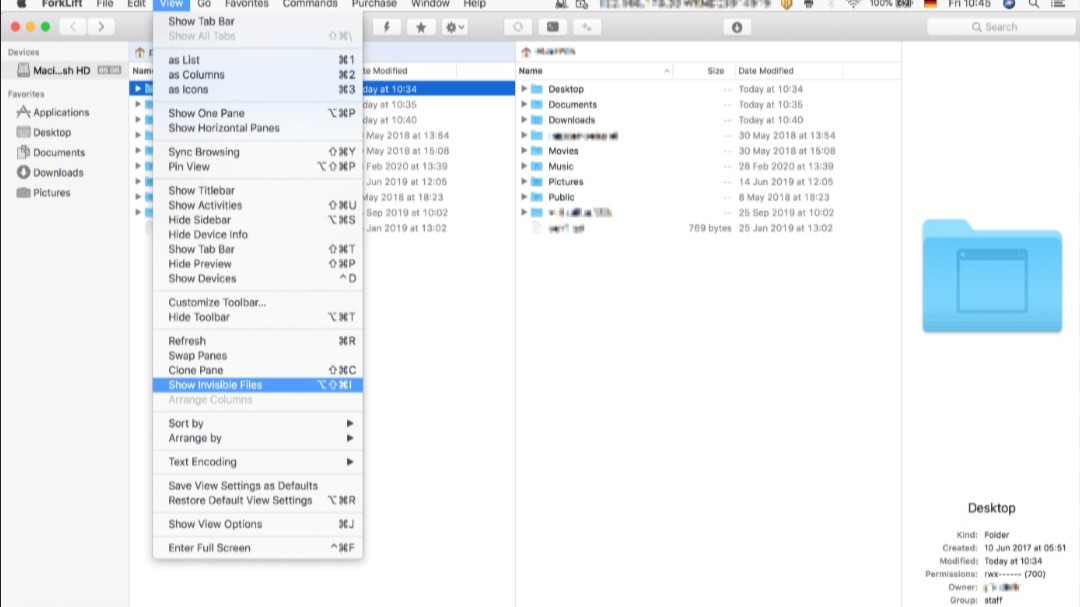
Revealing Hidden Files
Revealing hidden files can be a tricky task for many computer users. Hidden files are typically files that are not meant to be easily accessible or visible to the average user. These files can contain important system information, personal data, or even sensitive information that should not be shared with others. It is important to understand how to properly reveal hidden files in order to ensure that you are not accidentally deleting or modifying important files on your computer.
There are various methods for revealing hidden files, such as adjusting settings in the file explorer or using command prompt commands. By revealing hidden files, you may gain access to additional information or settings that can help you better understand and manage your computer system.
However, it is crucial to proceed with caution when revealing hidden files, as making changes to these files without proper knowledge or understanding can potentially harm your computer system or compromise your data security. Overall, revealing hidden files can be a useful tool for computer users looking to gain a deeper understanding of their system, but it is important to approach this task with care and caution to prevent any unintended consequences.
Final Thoughts
As we come to the end of our discussion, it is important to reflect on the various perspectives and arguments presented. It is clear that there are differing viewpoints on the issue at hand, with valid points being made on all sides. It is crucial to consider the implications and consequences of our decisions, as they can have far-reaching effects on individuals and society as a whole. It is also important to remember that there is rarely a black and white answer to complex issues, and that we must be willing to engage in thoughtful dialogue and debate in order to reach a deeper understanding.
In conclusion, it is essential to approach final decisions with an open mind, a willingness to listen and learn from others, and a commitment to finding solutions that are fair and just for all involved. Let us remember that our actions have the power to shape the world around us, and that it is our responsibility to act with integrity and compassion in all that we do.
